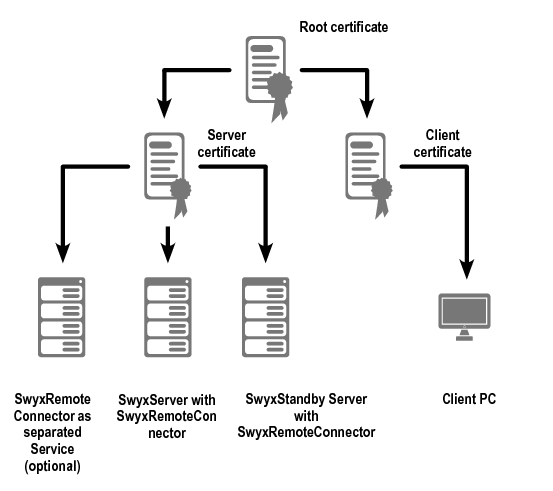

Root certificate | X509v3 Basic Constraints: critical CA:TRUE X509v3 Key Usage: Certificate Sign, CRL Sign |
Server certificate | X509v3 Basic Constraints: CA:FALSE X509v3 Key Usage: Digital Signature, Non Repudiation, Key Encipherment X509v3 Extended Key Usage: TLS Web Server Authentication |
Client certificate | X509v3 Basic Constraints: CA:FALSE X509v3 Key Usage: Digital Signature, Non Repudiation, Key Encipherment X509v3 Extended Key Usage: TLS Web Client Authentication |
Root certificate, public key only | Local computer memory ("Computer account") | Certificates (Local Computer) | Trusted Root Certificates | Certificates |
Server certificate (including private key) | Local computer memory ("Computer account") | Certificates (Local Computer) | Personal - Certificates | Certificates |
Client certificate (including private key) | Current user memory ("Own user account") | Certificates - Current User | Personal | Certificates |